Enable B2B users on an Azure AD B2C tenant
For one of our customers, we created a set of B2B applications using Azure Active Directory (B2B) and Azure App Service Authentication (EasyAuth). Now they want to enable customers on one of the applications while still enabling single sign-on for (external) business users on all applications. To accomplish this, we used Azure AD B2C and linked it with the existing Azure AD tenant that already contains all business users. In this blog I will describe the individual steps and missteps we made. I will focus solely on the Azure AD-configuration and leave out any other changes.
Let’s assume the Azure AD tenant and the AD B2C tenant including the app registration and user flows are created and focus on linking the active directory tenants.
Create an identity provider
First create an app registration in the Azure AD tenant. This app registration will function as the Identity Provider for the Azure AD B2C tenant. The redirect uri is the authentication response endpoint of the B2C tenant. This uri has the format https://<b2c-tenant-id>.b2clogin.com/<b2c-tenant-id>.onmicrosoft.com/oauth2/authresp.
Next configure a client secret. Remember the client id and the secret value since they are needed when configuring the identity provider in the B2C tenant.
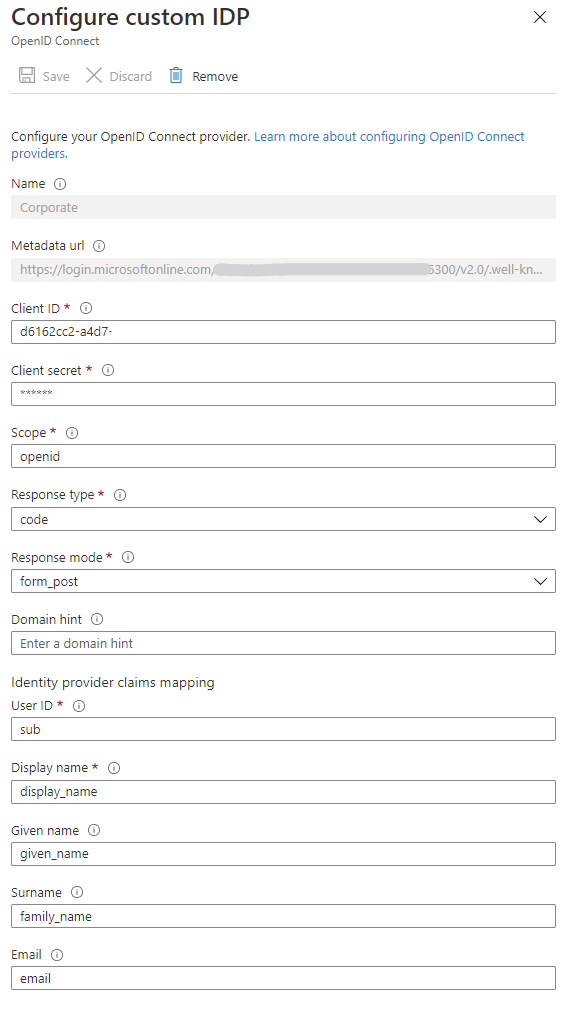
Switch to the B2C-tenant to create a new identity provider. Make sure it has a nice and recognizable name, since that name will be displayed on the sign-in and sign-up pages.
Provide here the client id and client secret of the app we just created and build up the metadata url based on the following template: https://login.microsoftonline.com/<b2b-tenant-id>/v2.0/.well-known/openid-configuration.
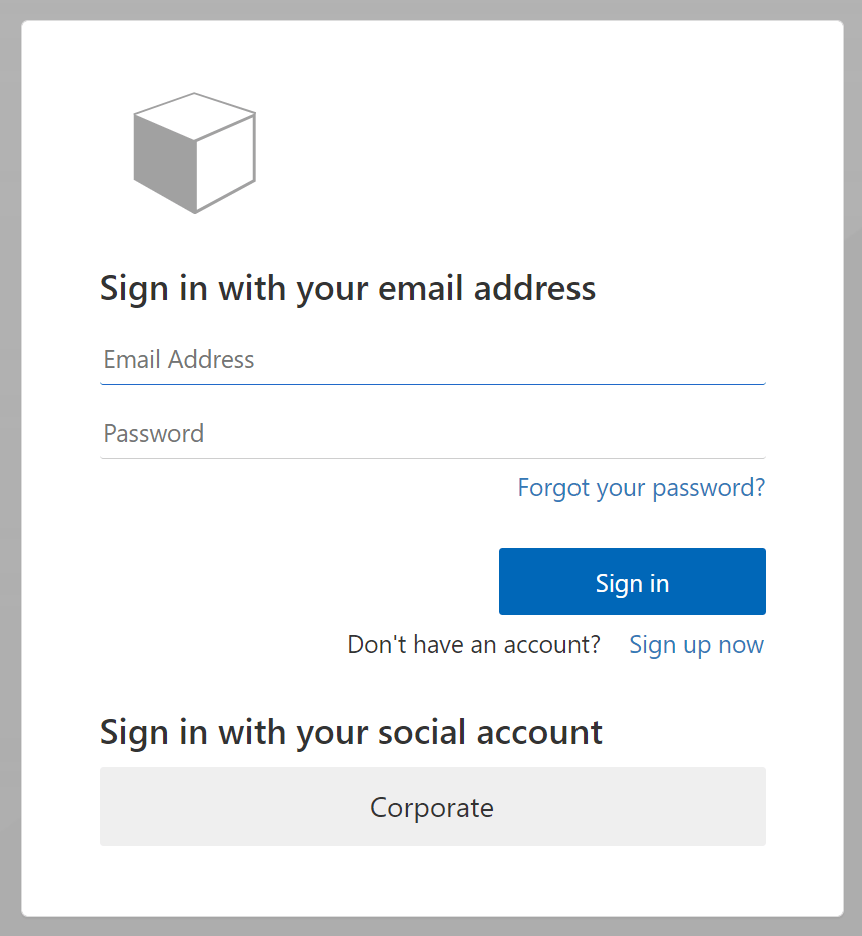
The last step is enabling the identity provider in the user flows. This is nothing more than selecting the OpenID Connect Identity provider in the required user flows. Do not forget to enable the identity provider in the sign up flow. See the ‘issues I ran into’ for more details. When testing the sign-in flow the ‘corporate’ sign-in button will be displayed.
Issues I ran into:
Deleting an identity provider
While preparing the blogpost, I removed an identity provider that was in use by a user flow. This caused the user flow to be hidden and it was almost impossible to get it back again.
Admin consent for B2B user
When signing in with a B2B account, the user is asked to consent. When the user has no admin privileges it will not be possible consent. Either an admin of his organization has to sign in first or you should give admin consent in the B2B App Registration on the Api Permissions-tab.
Signing in with B2B user
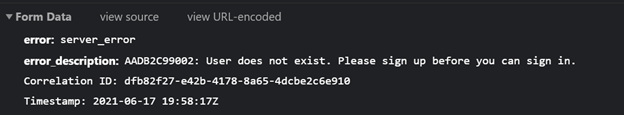
When signing in with a B2B user, I end-up with a 401-error on the ‘callback’-request to my application. When looking closer at the request in the network tab in the developer tools I discovered the following description:
Although it’s a business user registered in the B2B tenant, the user needs to sign up first. This will create the link between the B2C tenant and the B2B tenant. When using the combined sign-in and sign-up flow, the user will be registered automatically in the B2C-tenant.