
- Cloud
- Security
Azure Cloud Security 3: You Are Logging Everything — And Seeing Almost Nothing

- Cloud
- Security
Azure Cloud Security 2: Identity Is the Perimeter You Forgot to Guard

- Cloud
- Security
Azure Cloud Security 1: The First Security Conversation You Have Too Late: Hardening an Existing Azure Environment
- Cloud
- Machine learning & AI
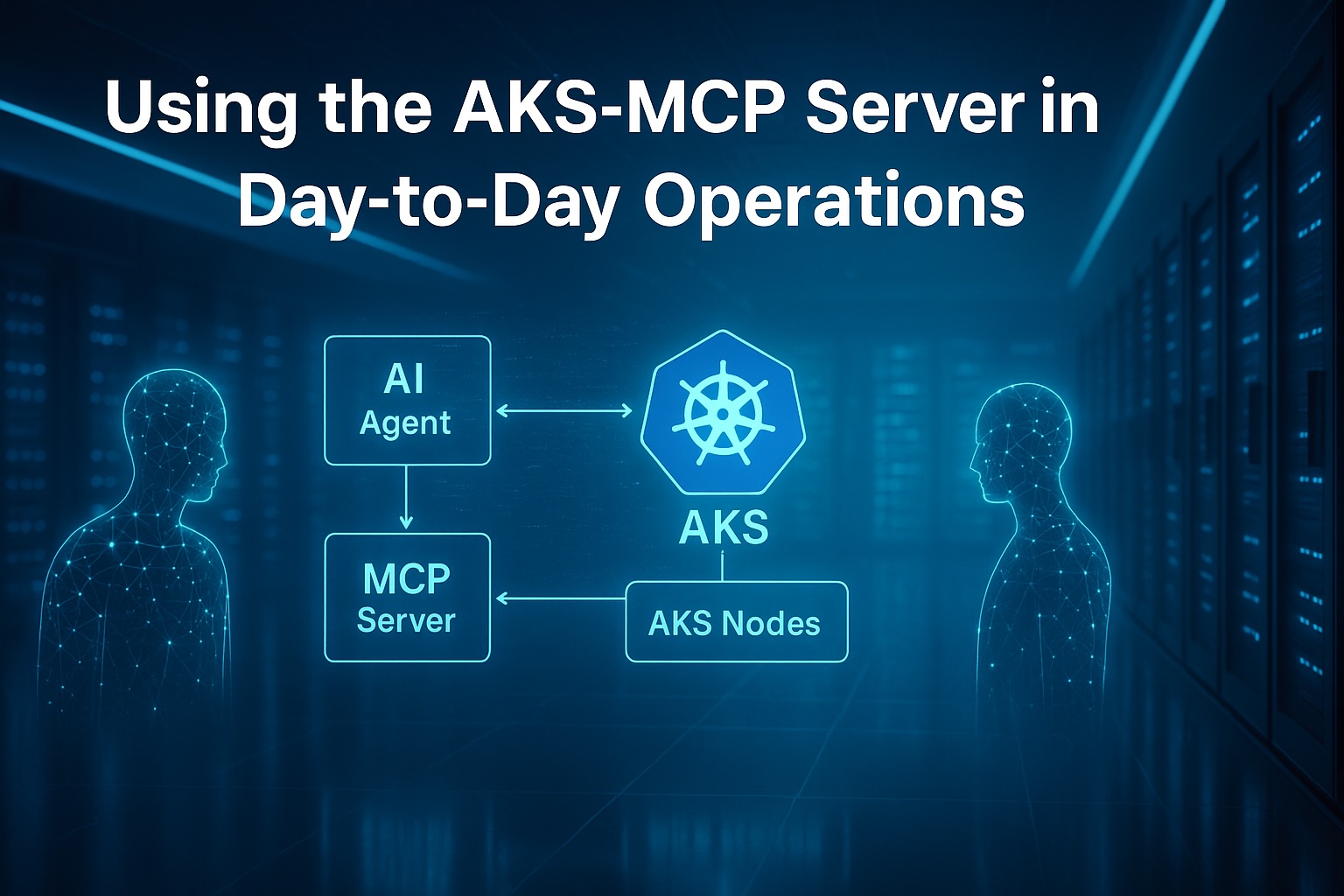
Using the AKS-MCP Server in Day-to-Day Operations

- Cloud
- Security
Azure Kubernetes Security Demystified: From Nodes to Pods

- Cloud
Harnessing Chaos: Implementing Chaos Engineering with Azure Chaos Studio and Gremlin on AKS

- Cloud
Digital Sovereignty and the Public Cloud: Navigating Azure in a European Context

- Cloud
Azure Kubernetes Chronicles part 5: Autoscaling with KEDA

- Cloud
From Code to Cloud: A Hands-On Guide to Azure Container Apps

- Cloud
Azure Kubernetes Chronicles, part 4: Dataprotection

- Cloud
Azure Kubernetes Chronicles, part 3: Observability

- Cloud
Azure Kubernetes Chronicles, part 2: Networking using eBPF

- Cloud
Azure Kubernetes Chronicles, part 1: Container Network Interfaces

- Cloud
Challenging the Cloud Cost-Saving Myth: A Closer Look at Azure and cost control

- Security
Zero Trust in the Cloud
Want to know more about our services?
We are your dedicated partner. Reach out to us.

